Under Control Game Facebook Cheats
- The ultimate FaceBook cheats resource. We have the latest FaceBook cheats, FB cheat codes, tips, walkthroughs and videos for FB games.
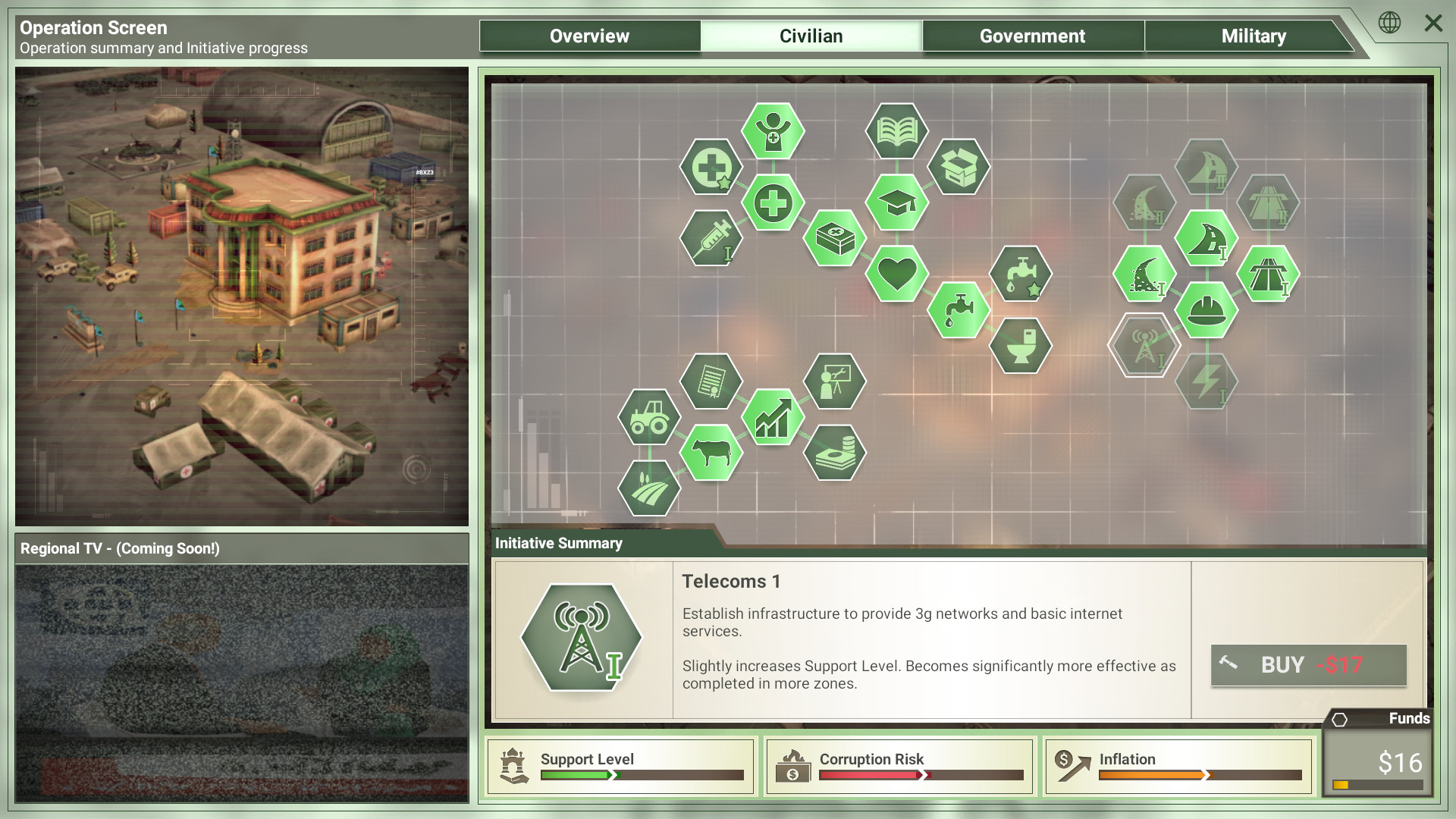
- How to use this CHEAT TOOL??? 1.Log in on your Facebook account and launch the game 2.Run the “ Under Control CHEAT TOOL” and press “Login” button to connect to game account. 3.Enter amount of Gold, Food, Money, Fuel, Diamonds and other options to be added to your account and press “ADD” button.
- You can submit new cheats for this game and help our users gain an edge. Have We Been Fooled? You can submit a problem report for any non-working or fake code in the lists above.
- Facebook Game Cheats Free
- Under Control Game Facebook Cheats Age Of Empires 2
- Control Game Cheat Table
Almost any internet user at least once in their life thought about to hack Facebook password of someone from their friends list. This is not case just with FB, but with any other social network account too.
In most cases it’s about people who are in relationship who wants to check out if their partner is cheating on them. So their goal is to break inside a Facebook account and read messages and chat logs with any suspicious people to find out the truth.
But in overall reasons are different. Some people just forget their login details, including their email address too. So without it it’s almost impossible to get an account back. Some people get hacked, and so on.
Under Control Fans. 447,558 likes 741 talking about this. An insane mix of dynamic combat, construction and development, as well as real-time PvP fights!
Today we are going to show you the working and tested methods to hack into a Facebook account, ranked from most reliable one to less.
How accurate are these methods? That depends on which way you decided to go for. Some of these are doing the job by itself, like cracking tools. So all you have to do is to enter a details and let the application do its job by itself.
However some methods require a bit of thinking and tricking your victim to fail on your “trap” in aim to get their password.
So let’s get started.
Quick navigation:
1. With using a special software Tool v.2.9.0.
2. With a Keylogger
3. Hack Facebook with a Phishing method
3.1. How to make a Facebook phishing page
1. Using a special software “Tool v.2.9.0.”
At this time this is the most reliable method to get login password of almost any existing Facebook account.
How this is even possible?
An anonymous group of programmers who are hacking online accounts on marketplace section of well know HackForums.net decided to make something in return for they fellows to celebrate their decade of successful hacking existence.
This freeby they called the Tool v.2.9.0, which is an application made to crack Facebook passwords using a customized well known brute-force method.

For those who don’t know a brute-forcer is a tool which attacks a login page with hundreds or even thousands attempts of possible combinations of usernames and passwords previously added into textual file which user needs to connect with a bruteforcer. Those passwords can be randomly created by a software or manually typed. A stronger and faster bruteforcers requires more CPU power.
What is different with the Tool v.2.9.0. is that it has a special method of bruteforcing added inside. And a difference is that an IP address gets changed after every 3 unsuccessful login tries. This is because Facebook security system will block you from further logging in if you fail to get into your profile 3 times with a false password. You will have to wait few hours to try again. And if you fail to login successfully again, your account can even get locked and then you will have to confirm your real identity by uploading some of your ID documents to Facebook representatives to confirm you are a legitimate owner of your profile.
Why some FB accounts can’t be hacked with this program?
Some accounts are protected then others of “normal Facebook users”. For example accounts of Mark Zuckerberg and many other well known celebrities with a blue tick icon as a prefix before their name has an extra decrypted system inside their accounts source code which automatically recognizes any hacking attempt done by a software.
Facebook Game Cheats Free
But hacking any account of normal users still works fine.
NOTE: Keep in mind that these brute-forcing apps often gets patched and stop working after some time when official spam team detects they’re dangerous and decide to do something to stop it in aim to protect their users’ privacy and safety.
So until then we will be checking regularly if the Tool v.2.9.0. still works or not. And if it gets patched we will add notification here that it got blocked.
Status: Still working
Tested on: June 16, 2020.
You can download Tool v.2.9.0. from its official website by clicking the button below.
App works on Windows, Mac, Android APK and iOS. You can choose your version at downloads page.
2. Using a Keylogger
First let’s clear what a keylogger actually is (For those who don’t know).
This is an application which monitors keystrokes typed on a keyboard and saves these logs in a textual documents which can be automatically uploaded to admin’s email (or some other kind) online account.
Purpose of keyloggers existence are various, like to help monitoring children for their safety, to keep an eye of employees inside a company, or just to store your own personal logs for safety. And of course in our example is to spy other people in aim to find their Facebook password.
Keyloggers can be manually installed on a device or remotely. And they are available as desktop and mobile applications.
So if you’re thinking about how to hack someones Facebook account with a keylogger your main goal is to successfully install it into your victim’s device (Smartphone or PC).
To manually install it, you need to have a physical access to their phone or computer. Catch a right moment when a person goes somewhere, like on toilet etc, to grab a chance and plant your precious seed inside their device.
Keep in mind to open their antivirus software (If they have it installed) to add your keylogger to trusted zone because else it can soon be detected as a malware and deleted. Because antiviruses detects these kind of apps as spyware (which they actually are). Only some rare HQ keyloggers are FUD (Fully Un-Detectable) by all antiviruses. But for these you have to pay big price. Others low budget or free ones are often detected by a high rate by most of antivirus software.
After you’re done with this hardest step above, you’re ready to begin monitoring logs. As soon as your potential victim logins to their FB profile with a login information, you’ll be able to see their password inside a log.
Our recommendation would be not to get FB password only, but go for their email account password as well. This way if you have an access to their e-mail account which they’ve used to sign up for Facebook, even if they change their Facebook password you can always get it back if you have an access to their email as well.
What keyloggers are best to use?
We recommend Ardamax for desktop use and MSpy for mobile phones. However feel free to use any other if you think it’s better for your needs.
But make sure to always download them from official websites because keyloggers uploaded on other free-to-get sources are in 99% cases backdoored with other spyware which will infect your own device. So you will become a victim of your own trap. Be very careful!
3. Hack Facebook with a Phishing method
Phishing is a way to trick user to login to a fake website which looks exactly like an official one from where you want to get their password. Here we are talking about Facebook.
So our goal will be to make our victim think they’re logging into real Facebook home page.
How we are going to make them do this?
You need to think outside the box. But some already popular methods are sending them an email, WhatsApp, SMS or some other kind of message which says something like “Confirm you are active Facebook user by logging from this link” And the link is your phishing link which leads to a false Facebook login page. You will learn how to make a “phisher” in a next paragraph below.
However you can choose some other trick which works best for you. Just make them think they need to login to their FB account because of “something” important. Like to confirm their ownership or something else. Use your head 🙂
How to make a Facebook phishing page
Step 1:
Go to www.facebook.com (You need to be log out of your account). Refresh a page if you just logged out.
Now press a right click on your mouse somewhere on the page (Or press CTRL+U on your keyboard) and click “View page source”. In a new tab you’ll be able to see the whole source code of Facebook login page.
Select the whole text (CTRL+A) and copy it (CTRL+C or mouse right click > Copy).
Step 2:
Open your Notepad program (Start > Programs > Notepad) and in a new window paste the text you copied from the Facebook source page (CTRL+P or mouse right click > Paste).
Step 3:
Now with your mouse left button click to the top above the text inside the Notepad, then press CTRL+F and in a search box type “action=” without quotation marks, and click the “Find next” button.
There are two “action=” in the whole text. You need the first one. You can see how it looks in the picture below.
Replace the link inside the quotation marks you can see in the picture below with the “post.php”. Do not touch the quotations but only the text inside, as you can see in the examples below.
Now go to File > Save as and name your file “index.html”. Also make sure to set the encoding option to “Unicode”. See how it looks like in the pic below.
Step 4:
Now you need the post.php file. You can download it here.
Don’t forget to unzip it from the archive .rar file before uploading it to a server in the next step.
The password to open this .rar archived file is “OpenMe123”.
You’ll need the WinRar program to open this file. If you don’t have it installed, you can download it here.
Step 5:
Now you need to have two files, index and post ones.
You need to upload these to your web hosting account. There are free and payed hosting options. If you don’t have a paid hosting already you can register yourself a free one at www.000webhost.com.
(NOTE: Hosting is used to host files if you have a website. Since phishing page is also some kind of website, you should register yourself a hosting account, in this example at www.000webhost.com)
After you’re done with registration at www.000webhost.com, go to the “File Manager” folder. Inside you should see an empty “public_html” folder. In that folder upload two files “post.php” and “index.html”.
Now you are ready to test your phisher. After you registered your www.000webhost.com account you needed to make your unique username and get your custom link. Go to that link now and you should see a Facebook home page. If you can’t, means you did something wrong. Check all the steps again and try to fix your mistake.
If you still need help, feel free to comment about your problem below and I’ll be glad to assist you for help.
After someone types their login details inside your phishing page, you can find their FB login info inside a new created file called “usernames.txt” inside a same folder where first two files are uploaded.
And now you are ready to spread your link to your friends and catch their passwords!
I hope you found this guide helpful. As of today these are the most reliable and working methods to hack Facebook password successfully. If some new ones gets released they’ll be included here too.
Thanks for reading and have a nice day!
Disclaimer
Since I’ve noticed many people misuse this information in wrong manners which I didn’t approved when I shared this tutorial, I have to protect myself legally and write next disclaimer policy down.
By reading this tutorial you’re agreeing to use learned information for educational purposes only, which means you will only use it to recover back your own FB account of which you’ve forgot password or your account got lost by other reasons.
Using this tutorial in illegal activities, which is hacking Facebook accounts of other people without their prior permission is against law in every country. And by doing so you are doing it at your own risk.
WebRevelador is not responsible for any unallowed and illegal usage of information contained in this this tutorial.
WASHINGTON — Contradicting his secretary of state and other top officials, President Donald Trump suggested without evidence that China — not Russia — may be behind the cyber espionage operation against the United States and tried to minimize its impact.
In his first comments on the breach, Trump scoffed at the focus on the Kremlin and downplayed the intrusions, which the nation’s cybersecurity agency has warned posed a “grave” risk to government and private networks.
“The Cyber Hack is far greater in the Fake News Media than in actuality. I have been fully briefed and everything is well under control,” Trump tweeted Saturday. He also claimed the media are “petrified” of “discussing the possibility that it may be China (it may!).”
There is no evidence to suggest that is the case. Secretary of State Mike Pompeo said late Friday that Russia was “pretty clearly” behind the operation against the United States.
“This was a very significant effort and I think it’s the case that now we can say pretty clearly that it was the Russians that engaged in this activity,” Pompeo said in the interview with radio talk show host Mark Levin.
Officials at the White House had been prepared to put out a statement Friday afternoon that accused Russia of being “the main actor” in the hack, but were told at the last minute to stand down, according to one U.S. official familiar with the conversations who spoke on condition of anonymity to discuss private deliberations.
It is not clear whether Pompeo got that message before his interview, but officials are now scrambling to figure out how to square the disparate accounts. The White House did not immediately respond to questions about the statement or the basis of Trump’s claims. The State Department also did not respond to questions about Pompeo’s remarks.
Throughout his presidency, Trump has refused to blame Russia for well-documented hostilities, including its interference in the 2016 election to help him get elected. He blamed his predecessor, Barack Obama, for Russia’s annexation of Crimea, has endorsed allowing Russia to return to the G-7 group of nations and has never taken the country to task for allegedly putting bounties on U.S. soldiers in Afghanistan.
Under Control Game Facebook Cheats Age Of Empires 2
“The president has a blind spot when it comes to Russia,” said Sen. Mitt Romney, R-Utah. He told NBC’s “Meet the Press” on Sunday that Trump “doesn’t want to recognize Russia as the problem they are and the extraordinary bad actor they are on the world stage. … The reality is Russia really is a geopolitical adversary. They go against us on every front.’’
Pompeo in the interview said the government was still “unpacking” the cyberespionage operation and some of it would likely remain classified.
“But suffice it to say there was a significant effort to use a piece of third-party software to essentially embed code inside of U.S. government systems and it now appears systems of private companies and companies and governments across the world as well,” he said.
Though Pompeo was the first Trump administration official to publicly blame Russia for the intrusion, cybersecurity experts and other U.S. officials have been clear over the past week that the operation appears to be the work of Russia. There has been no credible suggestion that any other country — including China — is responsible.
Democrats in Congress who have received classified briefings have also affirmed publicly that Russia, which in 2014 hacked the State Department and interfered through hacking in the 2016 presidential election, was behind it.
It’s not clear exactly what the hackers were seeking, but experts say it could include nuclear secrets, blueprints for advanced weaponry, COVID-19 vaccine-related research and information for dossiers on government and industry leaders.
Russia has said it had “nothing to do” with the hacking.
While Trump downplayed the impact of the hacks, the Cybersecurity and Infrastructure Security Agency has said it compromised federal agencies as well as “critical infrastructure.” Homeland Security, the agency’s parent department, defines such infrastructure as any “vital” assets to the U.S. or its economy, a broad category that could include power plants and financial institutions.
One U.S. official, speaking Thursday on condition of anonymity to discuss a matter that is under investigation, described the hack as severe and extremely damaging.
“This is looking like it’s the worst hacking case in the history of America,” the official said. “They got into everything.”
Trump had been silent on the hacks before Saturday.
Deputy White House press secretary Brian Morgenstern on Friday declined to discuss the matter, but told reporters that national security adviser Robert O’Brien had sometimes been leading multiple daily meetings with the FBI, the Department of Homeland Security and the intelligence agencies, looking for ways to mitigate the hack.
“Rest assured we have the best and brightest working hard on it each and every single day,” he said.
The Democratic leaders of four House committees given classified briefings by the administration on the hack have complained that they “were left with more questions than answers.”
“Administration officials were unwilling to share the full scope of the breach and identities of the victims,” they said.
Pompeo, in the interview with Levin, said Russia was on the list of “folks that want to undermine our way of life, our republic, our basic democratic principles. … You see the news of the day with respect to their efforts in the cyberspace. We’ve seen this for an awfully long time, using asymmetric capabilities to try and put themselves in a place where they can impose costs on the United States.”
What makes this hacking campaign so extraordinary is its scale: 18,000 organizations were infected from March to June by malicious code that piggybacked on popular network-management software from an Austin, Texas, company called SolarWinds.
It’s going to take months to kick elite hackers out of the U.S. government networks they have been quietly rifling through since as far back as March.
Experts say there simply are not enough skilled threat-hunting teams to duly identify all the government and private-sector systems that may have been hacked. FireEye, the cybersecurity company that discovered the intrusion into U.S. agencies and was among the victims, has already tallied dozens of casualties. It’s racing to identify more.
Control Game Cheat Table
Many federal workers — and others in the private sector — must presume that unclassified networks are teeming with spies. Agencies will be more inclined to conduct sensitive government business on Signal, WhatsApp and other encrypted smartphone apps.
If the hackers are indeed from Russia’s SVR foreign intelligence agency, as experts believe, their resistance may be tenacious.
The only way to be sure a network is clean is “to burn it down to the ground and rebuild it,” said Bruce Schneier, a prominent security expert and Harvard fellow.
Florida became the first state to acknowledge falling victim to a SolarWinds hack. Officials told The Associated Press that hackers apparently infiltrated the state’s health care administration agency and others.
SolarWinds’ customers include most Fortune 500 companies, and its U.S. government clients are rich with generals and spymasters.
___
Associated Press writers Frank Bajak in Boston, Eric Tucker in Washington and Bobby Caina Calvan in Tallahassee, Florida, contributed to this report.